Azure Active Directory: Sign In Once, Use Cloud Inventory Management
Unified Cloud Environment
Combine all cloud services in one environment
User Management
Simplify user administration
Software-as-a-Service
No installation or configuration required
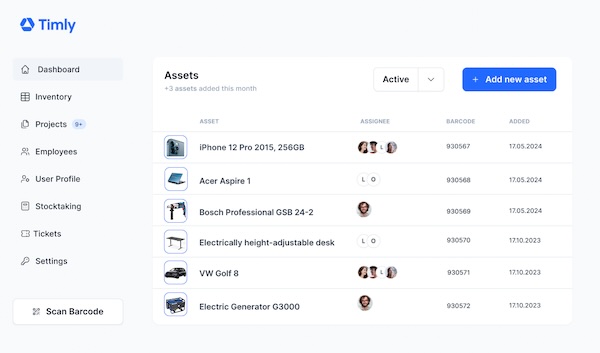
Inventory Management
Manage inventory with a cloud service
Enhanced Security
Includes numerous security features
Greater Convenience
Sign in once, access all cloud services
Cross-Service Cloud Administration
Active Directory as a Foundation
With Active Directory (AD), you can structure your company in a proven way. Microsoft Azure and Entra ID also use AD for their cloud service platforms.
Unified User Management
User and permission management is standardized across all integrated services, ensuring a consistent and organized approach. This not only saves time by reducing administrative effort but also enhances clarity, making it easier to oversee and control access rights across the entire system.
Integration via REST API
Timly can be securely integrated into Azure Active Directory via the established REST API. Once connected, users can access it with a single sign-on to Microsoft services.
Centralized Administration
This approach centralizes administration, conserving resources, increasing efficiency, and streamlining workflows.


Single Sign-On: Security and Convenience


Secure Authentication
Microsoft’s Single Sign-On (SSO) provides state-of-the-art security mechanisms for authentication, including Multi-Factor Authentication (MFA) and passwordless login.
Simple Login Process
Users no longer need to remember multiple passwords or authentication methods for different applications. A single login to Azure AD is all it takes.
Identity Protection
The new Microsoft Entra ID Protection uses advanced machine learning to detect unusual user behavior early, identify potential security risks, and block unauthorized login attempts automatically.
Unified Access Management
In the central Azure AD admin center, administrators can define which services a user is allowed to access, ensuring a systematic and organized administration process.
Cloud-Based Inventory Management
Benefit from Software-as-a-Service
With Software-as-a-Service (SaaS), the application runs centrally on a cloud server. Users simply log in via a web browser and gain full access to all features.
Low Hardware Requirements
All computing power is provided by the server, allowing the service to be used on almost any internet-enabled device, including smartphones and tablets.
Easy Access from Anywhere
As long as an internet connection is available, inventory management can be accessed from anywhere—no connection to the company network is required.
Remote Access
Users are created in Azure AD and gain immediate access to all authorized cloud services. With Single Sign-On (SSO), one login is enough, simplifying access while enhancing security and efficiency.


Technical Documentation
Your Questions Answered
What are the advantages of using cloud services over local installations?
Cloud services eliminate the need for local administration. There is no need to install applications or updates on individual devices. All users operate within a unified environment and share a central data repository.
How is Timly integrated into Azure AD?
Access via the REST API must be enabled in Timly’s administration settings. A cryptographically secure token is then generated for user authentication. Integration can be done, for example, using Azure AD PowerShell.
Are cloud services secure enough to handle critical operations?
Security depends on professional administration and adherence to the latest security standards, as is the case with Timly. When properly managed, cloud services can be as secure as government tax portals or online banking. Using Azure AD further enhances security.
How do Multi-Factor Authentication and Passwordless Login work?
Multi-Factor Authentication (MFA) requires an additional verification method, such as a smartphone app or a smart card reader. This prevents unauthorized access even if a password is intercepted or a device is compromised. Passwordless login relies on biometrics or physical security keys, making password theft impossible.
Get to know all our functions
Explore Timly Today
Book an online demo - free and without obligation - or create your free trial account directly.
Not ready yet? 10-day trial access to our software ➟